This blog post is about Team Foundation Server (TFS) and is about the situation where you need remember to update your TFS Agent settings.
I will assume that you already have TFS setup and are just using HTTP and want to make things a bit more secure with HTTPS. I am also assuming that you will be using port 443 for HTTPS traffic.
To update TFS to use HTTPS you need to do a couple of things:
- Have a legitimate certificate installed on the server that you can bind to
- Have an IP address on the server and have firewall access setup to that IP address on port 443
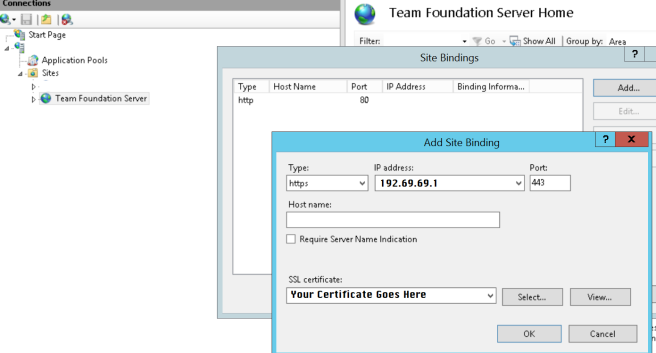
So in IIS we will add our new binding to our Team Foundation Server website:
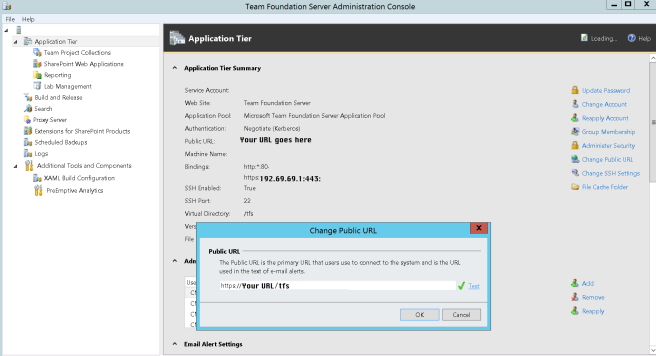
We will now go into TFS Administration Console to change our public URL. The added HTTPS binding will have flowed through from IIS and you should now see it in the bindings.
So now we have HTTPS working for our TFS instance. Users can connect to the new URL and we can utilise URL rewriting to direct anyone who forgets and uses HTTP.
Except our first nightly builds failed…
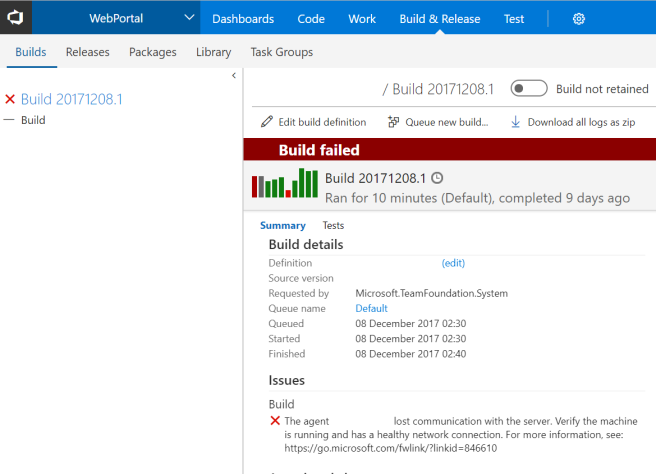
Looking at the diagnostic logs on the agent we can see the following (note the time is UTC time):
[2017-12-07 13:30:05Z ERR Program] System.Net.Http.HttpRequestException: An error occurred while sending the request. —> System.Net.Http.WinHttpException: A security error occurred at System.Runtime.CompilerServices.TaskAwaiter.ThrowForNonSuccess(Task task)
at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task)
at System.Net.Http.WinHttpHandler.<StartRequest>d__101.MoveNext()
— End of inner exception stack trace —
at Microsoft.VisualStudio.Services.Common.VssHttpRetryMessageHandler.<SendAsync>d__3.MoveNext()
— End of stack trace from previous location where exception was thrown —
The logs also showed that the agent was trying to go to the old address. So it was a simple change to the agent settings to point to HTTPS address.
Browsing to where the agent is installed we can now edit the .Agents file:
Within the .agent file we will change the following setting:
serverUrl: https://YourURL/tfs/
Kick off a queued build and it works as intended.
Yip.